SSL issues — how to deal with IIS and modern browsers requirements
It looks like Firefox and Chrome started to force the usage of TLS version 1.2. It is a good move and this also forces hosting providers to keep their infrastructure up to date. Some of our clients who are hosting their websites on-premises noticed that they also have something to do with their IIS configuration.
The symptoms
What are the symptoms of the issue? For instance, in Firefox you can see the following message:
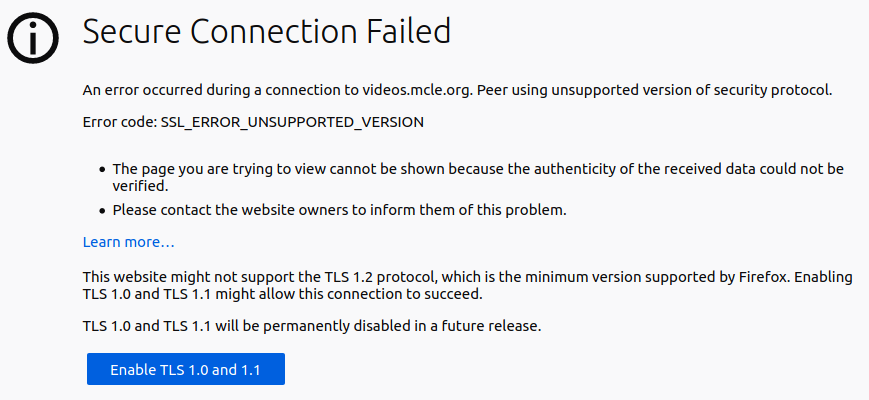
OK, you can tell Firefox to enable the older TLS versions, but will you ask all your users to do so? This is not the way to go. Also, if the recent TLS is not supported, most likely there is still an old SSL 3 or even SSL 2 enabled, which is bad too.
Steps to perform
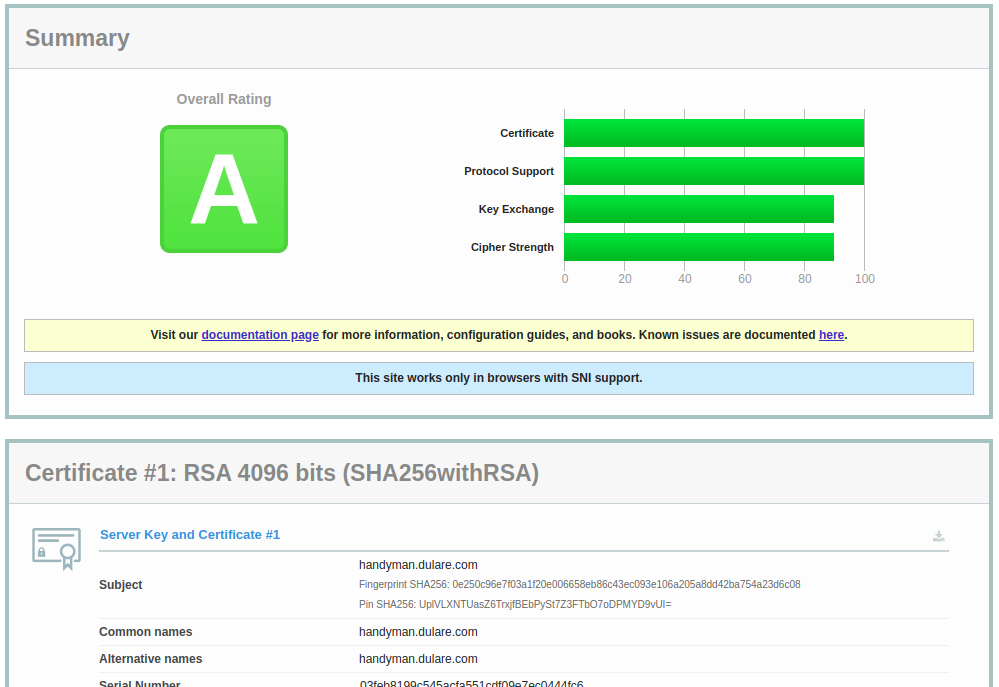
No matter what version of the webserver you are using, you should check your SSL health from time to time. My personal favorite is Qualys Labs SSL Server Test. Please note that you can test your own website, but you can also test the server you have problems with. Here is the sample result from the server that is configured properly:
And, to the contrary, here is the server that should be updated immediatelly:
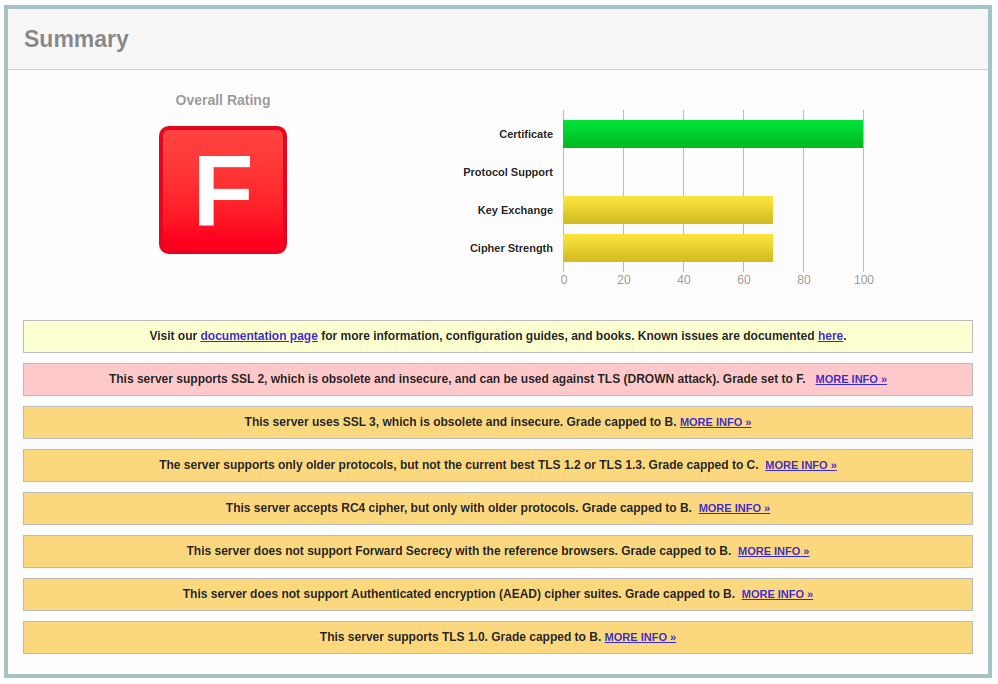
Take a look at how many issues were found – old protocol versions enabled, new ones not available… The list of issues is long and looks like there is a lot of work to do.
Once we have a diagnosis, we can act. There are several ways on how to enable TLS 1.2 or TLS 1.3 in IIS. There are also tutorials on how to disable old SSL 2 and SSL 3 in IIS. Most of them rely on the registry adjustments – you simply have to add some keys to the registry and remove or disable the ones which are responsible for old SSL versions. For some time I was using a ready-made REG file to implement these changes.
This changed recently. A colleague of mine showed me Nartac Software IIS Crypto. This is “is a free tool that gives administrators the ability to enable or disable protocols, ciphers, hashes and key exchange algorithms on Windows Server 2008, 2012, 2016 and 2019. It also lets you reorder SSL/TLS cipher suites offered by IIS, change advanced settings, implement Best Practices with a single click, create custom templates and test your website.” And yes, it does exactly as it says. You can simply download and install the tool, click “Best practices” and your IIS should be fine.
The tool is powerful – it gives you an ability to change the order of cipher suites, but for most users, the best practice setting should be enough. The additional advantage is that it comes also in the command line version. It is handy if you adjust multiple servers or simply want to add this tool to your maintenance scripts.